|
ipMonitor 6.1 Security | ||||||||||||||||||||||||||||||||||
| < Back | Index | Next > | ||||||||||||||||||||||||||||||||
By design ipMonitor probes computers, services, devices, and Internet software on Intranet and Internet networks. The activity of probing using various protocols and reporting Monitor status using HTTP presents little reason for concern regarding security. The following topics discuss in detail all security, features, precautions and concerns related to ipMonitor:
The following topics outline information you may require in order to adapt ipMonitor to your network environment. Access to ipMonitor via Web Browsers is secured with an Account Name and Password combination. ipMonitor accounts are self-contained, meaning user names and passwords are stored internally. ipMonitor has nothing to do with Windows NT Security and should not be confused with it. When a Web Browser first connects, it is challenged by ipMonitor and must respond with a valid Account Name and Password. After the user inputs their User Name and Password, the Web Browser transmits that information with each transaction between the Web Browser and the ipMonitor Web Server. Because ipMonitor account and password information is transmitted unencrypted, do not use NT network account names and passwords for ipMonitor. It is possible for hackers with sufficient knowledge and access to the network to intercept and reassemble packets into information. Subsequently they could find out username/password combinations(s) used to access ipMonitor. By entering completely unique user name/password combinations for ipMonitor accounts you can ensure that in the event that an ipMonitor account is discovered, no other critical network accounts could be compromised. Review the Firewalls & Proxy Servers section for more security details. If you are very concerned about security issues, please continue reading, ipMonitor can be secured to the point that only the local machine can view or control it. ipMonitor supports 3 types of internal accounts.
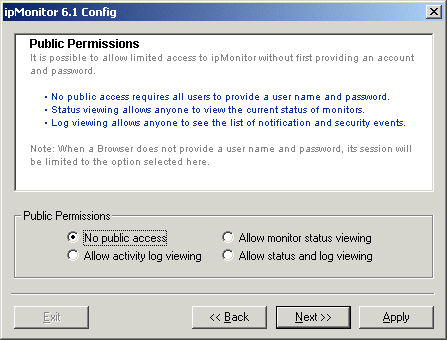
Disable Session After Failed Logon Attempts The "Global Settings" page includes an option to, "Disable session after "x" failed login attempts". This controls the number of times a user IP Address can attempt to log onto ipMonitor using an incorrect User Name and/or Password before the 15-minute lockout is executed. If the user makes an attempt to logon during the 15-minute lockout period, the counter is reset and the 15-minute lockout starts over. All security lockouts are logged to the ipMonitor Activity Log. This option is very discouraging to hackers and robots written to determine username password combinations. If Public Access is enabled, the "Monitor Status" and/or "Activity Log" pages can be accessed without a user name and password. This is similar to any Web site on the Internet that allows public access to some or all pages. Most ipMonitor configurations do not allow public access, often they only allow administrator accounts. On an Intranet for example, this public access feature might be used to inform network users regarding the state of a computer or service they might be having difficulty accessing.
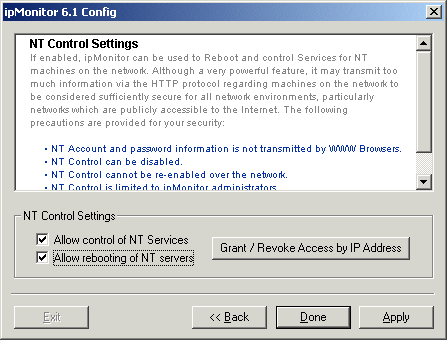
To disable Public Access completely, use the ipMonitor Configuration program and select "No public access" from the "Public Permissions" screen. ipMonitor is able to scan your network and locate computers by name, then display a list of NT Services for NT computers. Services can be stopped and started, as well NT computers can be rebooted. For some security schemes this feature might transmit too much information about computers on the network to be considered desirable.
By default, ipMonitor cannot be used to control Windows NT machines. The ability must specifically be turned on at the time of installation or later by using the ipMonitor Configuration program. The ability to stop and start NT Services as well as rebooting computers can both be independently enabled or disabled.
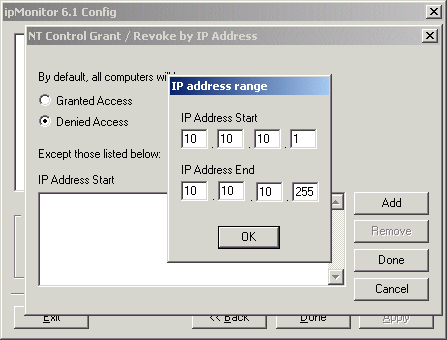
The ipMonitor NT Control functions have a built in lockout mechanism that uses IP-addresses to determine which machines can access the feature. Even if an administrator account has somehow been obtained, the intruder will still be locked out (if correctly configured). Anyone from any IP address other than those entered here will be denied access to the NT Control functions. Select the "Add" button to enter the start and end IP Addresses for the range you are defining. The example shows a single IP Address however IP ranges are also supported which allows you to define your internal network.
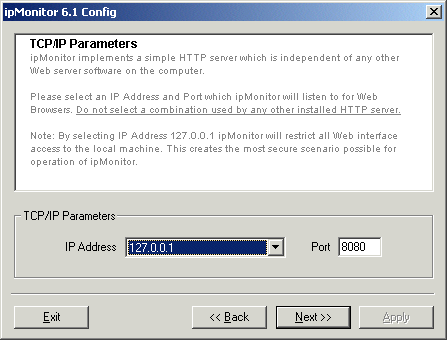
ipMonitor can be configured so that it can only be viewed or controlled from the local machine. It can still go about it's business of monitoring the enterprise, the interface just can't be accessed from any Web Browser except the one installed on the local computer. This security option provides the highest degree of control over access to the ipMonitor interface because it requires that anyone using the software must first be able to log onto the machine on which ipMonitor is installed. Most ipMonitor installations do not require this level of security and prefer the ability to use and configure the software from anywhere on the internal network.
The "ipMonitor Configuration" program is used to set "Local Access Only". This is done by entering, 127.0.0.1 for the IP Address ipMonitor will use to listen for Web Browsers. Within TCP/IP, IP Address 127.0.0.1 is reserved for local activity only, the protocol itself only routes local conversations using this IP. Firewalls provide a very high degree of network security. Please refer to the section titled Firewalls, Proxy Servers, Ports which discusses three ways to setup ipMonitor using a firewall so that both safe (internal) and militarized (external) zones can be monitored.
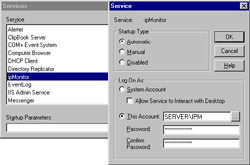
NT Security Relative to ipMonitor ipMonitor runs as a Windows NT Service. If ipMonitor is left to run in the default "LocalSystem" account for Services it will have no access to network functions. If you intend to use any of the features listed below, the ipMonitor Service must be configured to operate within an account which has access to the appropriate resources on the network.
Remember, if you are mapping resources on network computers, you must also go to the computer(s) and grant the appropriate permissions discussed in the following topics. ipMonitor used UNC file paths to monitor files on remote computers. If you accepted the default "LocalSystem" account:
Assigning an alternate account used to monitor files on remote computers using UNC file paths requires two steps. Note this is also the account ipMonitor must run within.
A bit more about UNC: UNC stands for "Uniform Naming Convention". It's a standard way to access network shares in NT and other Microsoft products. ipMonitor supports UNC, as opposed to Network-mapped drives, for the following very simple reason. NT only lets you map drives for logged-in users. Since ipMonitor runs as a service, it can't be a logged-in user, consequently it has no access to Network-mapped drives. The format of a UNC pathname is simple. <HOSTNAME> is the Network name. <SHARE-NAME> is what the drive or directory you are accessing is shared as, on <HOSTNAME>. i.e.: \\<HOSTNAME>\<SHARE-NAME>\To check permissions: You can do a simple check to see if ipMonitor can get to a directory containing a file that is to be monitored. Do this by logging into NT as the user ipMonitor is running as and then type the following into the Run dialog (from the Start menu): \\<HOST>\<SHARE>\If this works, ipMonitor has permission to get into the directory. You can also open a file in notepad to see if you can read the file. Alternately, if you have installed the Windows Desktop Update with IE4 & 5, you can type the UNC pathname into Windows NT explorer. To allow permission to its own database and resource files the permissions for the ipMonitor directories must be updated to reflect your permissions scenario. An ODBC driver must be installed on both the ipMonitor computer and the SQL computer. ipMonitor must have permission to access to the ODBC driver on the local computer and must provide the expected ODBC Username and Password in order to monitor SQL data sources on remote computers. Username and password are entered at the time that the ODBC Monitor is created. Refer to your ODBC documentation regarding all other security details pertaining to ODBC drivers. NT Service and REBOOT Function For the NT Service and Reboot functions to work, the account that ipMonitor runs within requires Network Browsing ability and must have the following rights.
|
||||||||||||||||||||||||||||||||||